*Updated October 2022
Everyone suffered one way or another during the pandemic - businesses small and large lost money, and some even had to close down. Front-line workers risked their health every day, creative professionals lost profit opportunities, and everyone was pretty bummed out at one point or another.
Yet, there was a very specific “workforce” that thrived at the increased use of online platforms and became rather more creative than usual. These people actually started making more money and creating new products. And no, I’m not talking about Zoom - I’m talking about hackers.
Before the pandemic, 20% of cyberattacks used novel malware and methods to surprise targets. During the pandemic, this rose to 35% of newly-minted, never-before-seen attack vectors. Overall, 84% of organizations experienced some sort of phishing or ransomware threats last year.
And the attack vectors are becoming more sophisticated, too. Phishing moved beyond emails and onto the sphere of SMS and voice. Ransomware got combined with data leakage attacks to persuade targets to pay up. Even post-pandemic, there’s a 35% increase in ransomware attacks, while the highest increase in cyber threats has to do with data exfiltration/leakage with a 55% increase.
In a nutshell - things are getting pretty serious. In the dramatic yet truthful phrasing of Chuck Brooks of Forbes:
“Ransomware came on with a vengeance targeting many small and medium businesses. Perhaps most worrisome was how critical infrastructure and supply [chains] security weaknesses were targeted and exploited by adversaries at higher rates than in the past.”
So, let’s delve into the ins and outs of ransomware - how it works, types of ransomware, who is behind it, who are the targets of ransomware, and some ransomware examples from the past.
What is ransomware?
Briefly, ransomware is a type of malware that holds some sort of information “hostage” for ransom - it may be withholding access to a computer network, databases, applications, or particular files. The malware that hackers use encrypts an organization’s critical data so that they can’t access it without paying out the ransom. It’s no secret that data is currency due to its financial value to businesses, NGOs, and government organizations, so hackers employ ransomware and data leakage attacks to extort money from them.

In fact, hackers use various types of ransomware to paralyze entire organizations and supply chains, as the malware quickly spreads throughout the network and hijacks access. A Palo Alto Networks Unit 42 report on ransomware from the first half of 2021 found that the average ransomware demand rose by 82% since 2020 and reached a staggering $570,000.
If you're curious about other companies similar to Palo Alto Networks you can browse through them here.
Malware vs. ransomware
In short, ransomware is malware. Malware - short for “malicious software” - is an umbrella term that includes viruses, trojan horses, spambots, worms, cryptojacking, etc., as well as ransomware. The distinguishing feature of ransomware is that it’s “malware when it is intended to create damage to a computer, network or server” and ultimately asks for a ransom in return for releasing the files. Ransomware is basically “ransom malware.”
How does ransomware work?
In short, ransomware employs symmetric or asymmetric encryption - a type of cryptography using a public-private key pair for file encryption and decryption. Recent types of ransomware attacks use both symmetric and asymmetric encryption to increase effectiveness, to the dismay of the victims of cybercrime.
[Related Article - Ransomware Attack Vectors and How to Protect Your Company]
The attacker shares the private key with the target only after they’ve paid out the ransom, though paying out doesn’t always ensure that the cyber criminal will stay true to their word. And in these cases, the victims of cybercrime never regain access to their data.
There isn’t just one type of ransomware - there are multiple variations, combinations, and vectors (channels) through which it’s launched. Ransomware is generally spread through emails, SMS, unsecured remote desktop protocol connections, and using social engineering, i.e., exploiting the “human factor” - though this list is not exhaustive.
Once the malware is inside the system, it remains there until its purpose is completed - searching valuable files and then encrypting them, sometimes spreading throughout the entire network of an organization. Once it’s spread, the attacker gives a 24-48 hour deadline to the victim to payout. Generally, in past ransomware examples, hackers demand untraceable means of payment, and recently cryptocurrency has been the most popular - up to $5.2 worth of Bitcoin can be attributed to ransomware payouts.
Monero emerges as crypto choice for cybercriminals
A newer cryptocurrency has become the go-to choice for cybercriminals: Monero, the privacy coin. The thing with Bitcoin is that it’s not exactly anonymous - it’s pseudonymous. This means that although a recipient's name is not cited, Bitcoin transactions can be tracked to the recipient’s wallet ID. With BTC, cybercriminals would have to go to certain lengths to cover their tracks and use Bitcoin mixers or tumblers to conceal the origin of the coins. Needless to say, this leaves a margin for error.
Monero, on the other hand, is private, untraceable, and secure. As much as people would like to focus on the fact that it eschews government surveillance, these traits have made it ideal for cybercrime, and it’s evident in ransomware examples. Consequently, Monero’s value has grown significantly in the last few years, and it’s become the sole accepted currency of cybercrime organization REvil.
Who is behind ransomware attacks?
Unfortunately, hackers aren’t the Robin Hoods of the digital age, upholding an iron-clad moral code about only stealing from the big bad, bringing down corrupt governments, or practicing vigilante justice. If these exist, they’re in the tiniest minority, and ransomware examples paint a different picture.
Mostly, you get joyriders or amateur hackers that get occasionally lucky, but on the other hand, you get professional, organized hackers that cost organizations millions of dollars in losses and government-sponsored hackers - but we won’t speculate on this last area.

So, rather than your friendly neighborhood hacker, we have criminal organizations investing in highly-profitable ransomware operations, according to the Unit 42 report. And while some claim that cybercriminals avoid extorting money from organizations in healthcare, education, nonprofit, or government - either because they haven’t the funds to pay up or to avoid a backlash of moral outrage - other findings and past ransomware examples say otherwise. Only two years ago, in 2020, the UVM Health Network couldn’t access their digital health records for a month due to a ransomware attack.
What’s more, cybercriminal groups like REvil, BlackMatter, and DarkSide have become increasingly organized and have launched large-scale attacks as well as pool together analytics data to identify the ideal US victim.
The results? This is what the writer of the Unit 42 report has to say:
“Ransomware attacks have prevented us from accessing work computers, pushed up meat prices, led to gasoline shortages, shut down schools, delayed legal cases, prevented some of us from getting our cars inspected and caused some hospitals to turn away patients.”
Past ransomware examples illustrate that cyberattacks can affect any sector and thus, anyone– education and healthcare are no exceptions. Black-hat hackers have become creative even in what they hold for ransom. According to SHRM, cybercriminals:
“…not only want money, but also threaten reputations by exposing attacks, blackmailing companies with the threat of exposing corporate or personal dirty laundry, and selling intellectual property to competitors.”
Who are the targets of cybercrime?
Though we will share some stats on the most highly targeted sectors, the broader truth is that anyone can be a victim of cybercrime. According to our head of data privacy, Jose Belo, sometimes professional hackers will target smaller companies with more lax security measures in order to go up the chain and make their way to the bigger parent companies. This means that the ransomware will be deployed and identified only once it’s higher up the food chain to do the most damage.
The same SHRM article we cited above supports this by saying that professional hacker groups are most interested in companies:
“...with at least $100 million in revenue and that are using virtual private networks, remote desktop protocols or tools from Citrix, Palo Alto Networks, VMware, Fortinet and Cisco.”
However, since medium-sized and especially small companies often lack the resources to set up sufficient defenses against ransomware threats, they’re also frequently targeted. As much as 43% of data breaches involve small and medium-sized companies, and only 14% of small businesses consider their defenses to be “highly effective.” And when we say anyone can be a victim of cybercrime, we mean it - in 2020, 61% of SMBs reported at least one cyber attack.
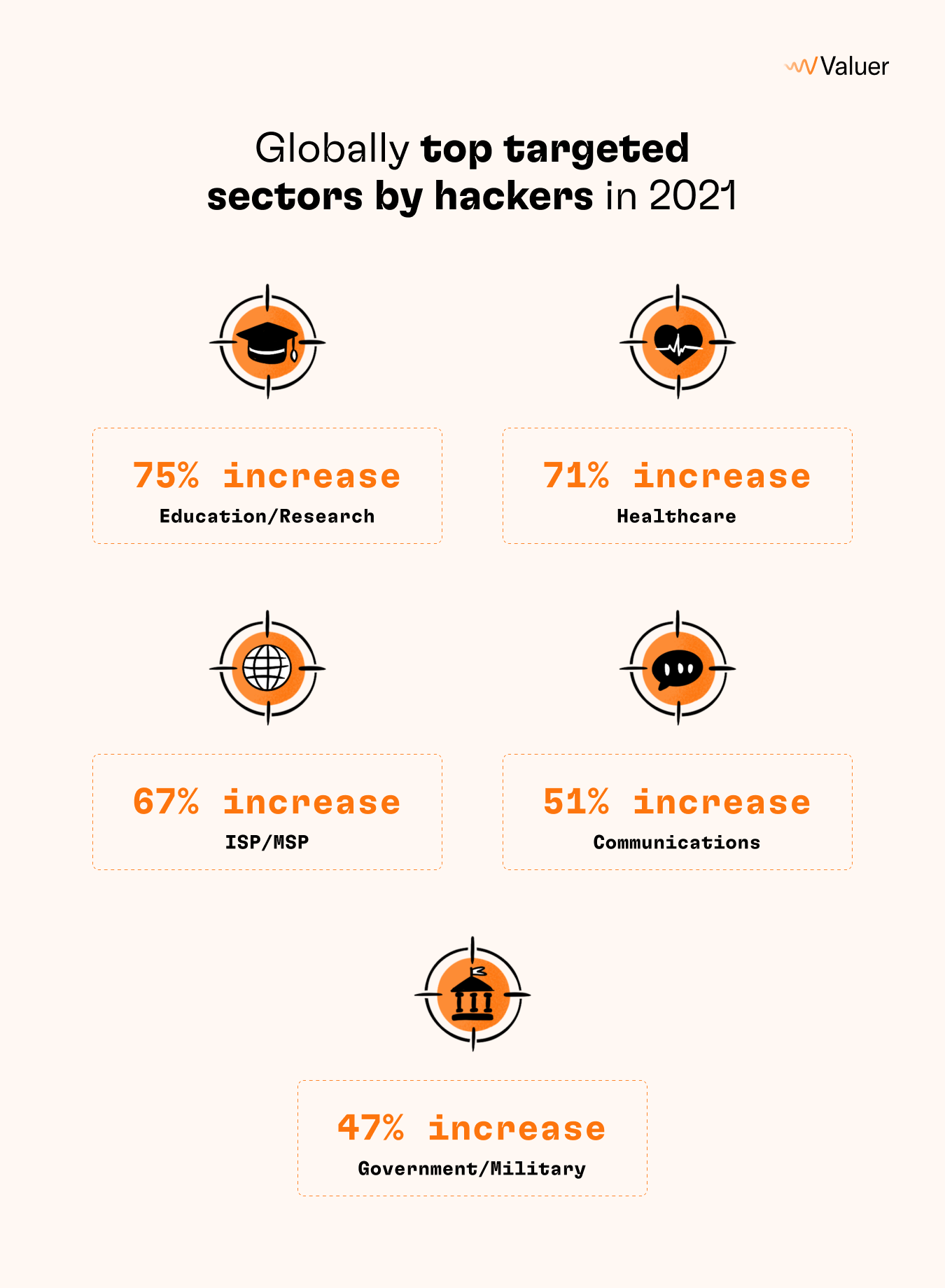
In general, the most targeted industries are banking, utilities, and retail. But in 2021, the highest increase in global hacker attacks occurred in the following sectors: education/research by 75%, healthcare by 71%, ISP/MSP by 67%, communications by 51%, and government/ military by 47%.
In another Forbes article, Chuck Brooks cites the healthcare, financial, and manufacturing industries as “soft targets” for hackers due to the vulnerabilities in these networks. Ultimately anyone can be a target, and according to Jose Belo, every company needs to be prepared for the worst.
Ransomware examples
The last decade is riddled with stories of ransomware that today serve as cautionary tales - especially since some of the malware is still in circulation. Most types of ransomware recently - meaning from 2017 onwards - use hybrid encryption, i.e., a combination of symmetric and asymmetric encryption. Here are some of the most hard-hitting ransomware attack examples and different types of ransomware:
Ryuk
Ryuk was launched in mid-to-late 2018 and amassed as much as $150 million from extortion by the end of 2020. It’s attributed to the WIZARD SPIDER hacker group, and it affected organizations in the healthcare, government, academia, publishing, manufacturing, and tech sectors. It all started when it infected Tribune Publishing and disrupted printing facilities across the US.
So, how does Ryuk work? Once it gains access to a system, this type of ransomware shuts down 40 processes and 180 services that could prevent it. Then it encrypts files using AES-256 but uses asymmetric encryption (RSA-4096) to encrypt the encryption keys so they can’t be accessed. Once it’s locked access to the files, Ryuk leaves the cybercrime victim with a TXT file ransom note. The malware can work remotely and take advantage of remote administrative shares.
WannaCry
WannaCry is one of the earlier and most damaging ransomware examples of this decade. It was launched in 2017 and wreaked havoc in over 150 countries within mere hours. The WannaCry malware spread so quickly that there’s reason to believe it was a coordinated cyberattack. The total ransom is estimated to be in the billions of dollars, paid in Bitcoin. The NHS alone suffered losses of over $100 million. Many individuals, government organizations, and large companies were affected, such companies as Nissan, Renault, and FedEx.
Interestingly, WannaCry didn’t spread through the usual route of phishing emails - but rather by exploiting a weakness in the Windows SMB (Server Message Block) protocol and using the EternalBlue exploit. Although Windows created a patch to fix the vulnerability, it took a while for users to install the updates. WannaCry took advantage of this period to spread: infected machines scanned the internet for other computers that lacked the patch and used EternalBlue to spread the malware to them.
Petya ransomware
Petya is more of a family of ransomware that includes NotPetya. It initially appeared on the scene in 2016 and was spread as email attachment malware. The start of Petya was “unremarkable,” but its successor, NotPetya, proved to be a very dangerous type of ransomware. In 2017, this variant caused over $10 billion in damages. It started by targeting organizations in Ukraine, including its national bank, and then spread throughout Europe and the US.
This ransomware encrypts the MFT (master file table) of a computer, which means that the victims lose access to all the files on their hard drive, including the computer’s operating system. The only thing they get to see is the ransom note.
Use ransomware examples as a cautionary tale
When we say you need to worry about ransomware, we actually mean this– you need to be prepared to face the threat of ransomware and other cyber attacks. This article isn’t about scaring you, it’s about showing you how important it is to ready your defenses. Mid-sized or small companies and startups may imagine that they’re not likely targets of ransomware attacks, but as we saw from today’s ransomware examples, anyone can be a target.
Cybercriminals will keep creating new types of ransomware and finding innovative ways to extort money. So we all have to be ready by improving our data security, creating cybersecurity compliance, training our employees, and employing numerous other defensive tactics. So, if you’re ready to learn all about these, head over to our article on how to protect your company from ransomware.
.png?width=103&height=103&name=Untitled_Artwork%20725%20(2).png)